A large application is like a machine that has been running for years without pause. You can’t just lift it, shake it apart, and expect it to keep working the next morning. That’s why moving a monolithic codebase to the cloud is never only a technical project. It’s about risk. The risk of downtime, broken dependencies, or hidden complexity catching you off guard.
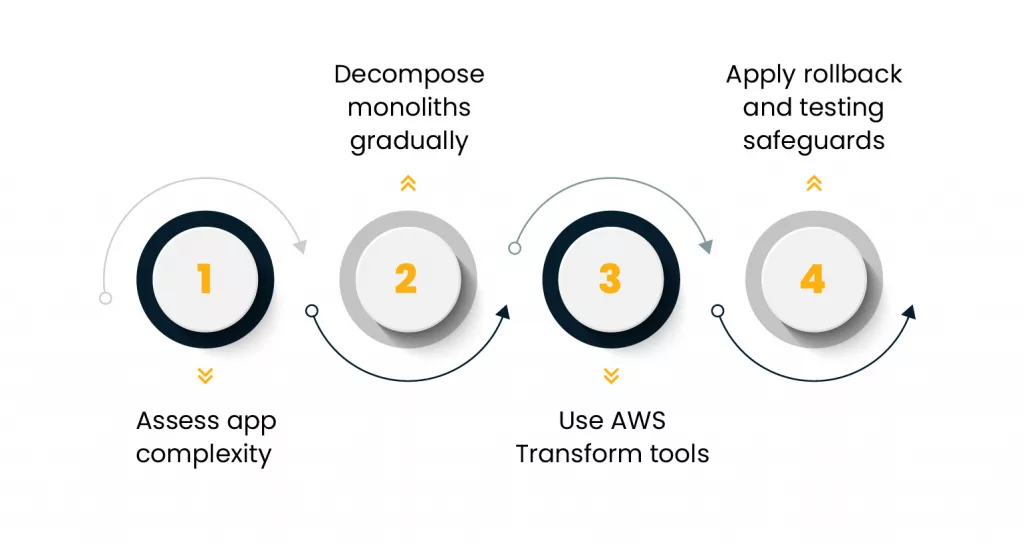
This post lays out a risk-first approach for teams taking on monolithic app migration with AWS Transform. Rather than rushing into code changes, you’ll see how to shrink the blast radius at each step. The four steps are simple: assess app complexity, decompose monoliths gradually, use AWS Transform tools, and apply rollback and testing safeguards. But behind each step is a set of practices that determine whether you reduce risk or multiply it.
Why monoliths carry hidden risks?
A monolith combines decades of design choices, developer shortcuts, and quick fixes into one big package. The code may run fine on-premises, but once you start moving it into AWS, every hidden dependency becomes a potential failure.
Two patterns drive most migration failures:
- Tight coupling of data and modules. When you move one part, others break unexpectedly.
- Unclear runtime dependencies. Cron jobs, third-party APIs, and shared SDKs often reveal themselves only after migration.
The task of monolithic app migration with AWS Transform is not just to port the code. It is to surface these risks early, make them visible, and reduce them wave by wave. This is also how your cloud transformation can progress without disrupting customer experience.
Step 1: Assess app complexity
Every successful migration begins with discovery. This is not the glamorous part, but it is where you build the map that guides every later step.
What to look for
- Code profile: Languages, frameworks, third-party libraries, and how current or outdated they are.
- Complexity hotspots: Modules with frequent changes, high bug counts, or dense logic.
- Dependencies: Internal APIs, scheduled jobs, shared components, and external SDKs.
- Data coupling: Shared schemas, cross-table joins, triggers, or hard-coded paths.
- Runtime profile: Traffic spikes, long-tail endpoints, latency outliers, and memory leaks.
- Release maturity: How often deployments break, how quickly fixes roll out, and whether teams trust their rollback process.
Why it matters?
Skipping this step is like migrating blindfolded. A finance company once tried to replatform its monolithic billing engine without discovery. They only realized two months in that critical reporting jobs depended on undocumented batch processes. The rollback cost them three extra months.
How AWS Transform supports this stage?
AWS Transform provides automated assessment reports:
- File types, lines of code, and cyclomatic complexity
- Dependency maps across services and libraries
- Suggestions for refactoring entry points
These reports act as a risk map. Teams can score each module and decide what to move first. For example, start with medium-complexity, low-risk functions while leaving core billing or authentication for later.
Diagram: Discovery flow
Repo Scan ─► Complexity Report ─► Heat Map ─► Wave Planning
Logs ─► Runtime Insights ─► Risk Score ─► Safeguards List
Data Map ─► Coupling Report ─► Candidate Selection
This upfront effort sets the stage for safer monolithic app migration with AWS Transform.
Step 2: Decompose monoliths gradually
Breaking down a monolith is not a single event. It’s a series of controlled cuts, each tested in production with minimal impact.
Good places to start
- Reporting modules with read-only access
- Batch jobs that can run independently
- Notification services like email or push alerts
- Search functions that can sit behind a proxy
- Authentication helpers that can be re-implemented as services
Patterns that reduce risk
- Strangler Fig: Route a small set of API calls to a new service while the rest stay in the monolith.
- Anti-corruption layer: Insert a boundary so new services don’t inherit old design flaws.
- Outbox pattern: Publish events from the monolith instead of writing directly into new services.
- Branch by abstraction: Add an interface inside the monolith, then swap implementations later.
Avoiding anti-patterns
- Big-bang rewrites: Rewriting the entire application before migration is almost always a failure path.
- Cross-cutting early: Don’t try to extract core payment or authentication first. Save those for later waves.
AWS Transform’s role
AWS Transform can analyze domain boundaries and suggest natural seams. For VMware estates, it also identifies tightly coupled groups of workloads so you can move them together, reducing breakage. This ability is central to risk mitigation AWS because it prevents fragmented migrations.
Diagram: Gradual cutover strategy
Monolith
│
├─ Proxy routes 5% of reads → Service A
├─ Batch job isolated → Service B
└─ Writes remain in monolith until validated
The gradual approach aligns with best practices in legacy app modernization, ensuring risk stays manageable.
Step 3: Use AWS Transform tools
Once the seams are clear, tooling makes the migration repeatable.
For .NET workloads
AWS Transform automates the shift from .NET Framework to modern .NET. It detects incompatibilities, proposes fixes, and even refactors certain blocks automatically. This is especially helpful for moving to Linux containers where possible.
For mainframes
Legacy COBOL code can be analyzed and translated into modern Java services on EC2 or containers. AWS Transform generates documentation as part of this, reducing reliance on shrinking pools of mainframe experts.
For VMware estates
VM dependencies are grouped into “waves.” These plans can be exported, edited, and re-imported for execution. By moving tightly linked systems together, you avoid partial outages.
Governance and visibility
Through AWS Migration Hub, you can track the progress of all migration waves in one place. This is vital for program leaders who must report on progress while keeping risk in check.
Cost
Currently, many core features of AWS Transform are free for AWS customers, lowering the entry barrier. This encourages teams to run pilots without large upfront commitments.
Diagram: AWS Transform agent workflow
Source Code + Inventory
│
├─ Assessment Agent → Risk & Complexity
├─ Planning Agent → Wave Plans
├─ Code Agent → Automated Fixes
├─ Validation Agent → Compile & Test
└─ Ops Agent → Runbook + Status in Migration HubThe automation doesn’t remove human decision-making. Instead, it makes monolithic app migration with AWS Transform more predictable.
Step 4: Apply rollback and testing safeguards
Even the best planning can’t predict everything. Rollback and testing safeguards ensure errors don’t turn into outages.
Practical safeguards
- Feature flags: Toggle features instantly without redeploying.
- Branch per wave: Keep risky changes isolated.
- Blue-green deployments: Maintain a known good environment in parallel.
- Shadow traffic: Replay live traffic to the new service without affecting users.
- Idempotent writes: Allow safe retries with unique identifiers.
- Data verification: Use checksums to validate migrated datasets before cutover.
- Kill switch: Always keep a one-click rollback path.
Database-specific patterns
- Read replicas: Keep new services updated in near-real time before cutting over.
- Dual writes with checks: Only for short periods, with strong reconciliation rules.
- Phased splits: Move non-critical tables first, then core business data.
Testing strategy
- Contract tests: Verify APIs match expected inputs and outputs.
- Golden path end-to-end tests: Ensure key customer journeys still succeed.
- Load tests: Stress new services before routing production traffic.
- Chaos injection: Simulate failures to confirm resilience.
Diagram: Traffic shift rollout
Start: 1% → Observe → 5% → Observe → 25% → 50% → 100%
Rollback if error rate exceeds threshold at any step
By combining these safeguards with AWS Transform, teams turn risky migrations into controlled experiments.
A risk-first blueprint
Here’s a condensed checklist for leaders planning their first wave:
- Pre-work: Run AWS Transform assessments, map dependencies, and build a risk heat map.
- Wave 0: Start with utilities and low-risk modules.
- Wave 1: Add read-heavy endpoints behind a proxy.
- Wave 2: Begin moving low-write services with independent data.
- Cutover: Shift traffic in controlled increments with rollback ready.
- Post-move: Archive unused code, document lessons, and prepare the next wave.
This approach reflects proven legacy app modernization practices while aligning with risk mitigation AWS principles.
Closing thoughts
Migration is never about speed alone. The safest teams move in waves, test constantly, and keep rollback simple. With the right safeguards and AWS Transform, you can modernize monoliths while protecting business continuity. Your next step could be as small as running a discovery scan and producing a one-page risk heat map. That single page will guide the rest of your monolithic app migration with AWS Transform journey and ensure your cloud transformation is steady, not shaky.