A modernization program can fail on day one, long before the first workload goes live. Not because the code is bad. Because one IAM permission was “temporary,” one bucket policy was copied from a forum, and one CI/CD job ran with keys that never should have existed.
That is why AWS security by design is not a checklist you add near the end, but a core part of any serious AWS modernization program. It is the structure that keeps modernization from turning into a risk of migration.
This blog is written for teams modernizing AWS who want to speed without surprises. The USP is simple: instead of repeating “best practices,” it gives you a working mental model you can use in real programs. It also includes a few lightweight diagrams you can copy into your internal docs.
Why must security be built in during modernization?
Modernization changes the ‘shape’ of risk, especially when enterprises move toward cloud-native architectures on AWS.
A monolith moving to containers changes identity boundaries. A data warehouse moving to lakehouse changes who can query what. A lift-and-shift to EC2 changes network controls. Every architectural decision changes the blast radius.
If security is treated as a gate at the end, you end up with two bad options:
- Delay launch while controls are retrofitted.
- Ship on time with exceptions that never get closed.
AWS security by design avoids both. It treats security as an engineering constraint, like latency or availability. You design it early, then enforce it continuously.
A simple principle
Modernization is a chain. The weakest link is usually not a missing tool. It is an unclear decision.
So, the goal is not “more security tooling.” The goal is decision clarity:
- Who can do what
- From where
- On what data
- With what proof
- With what logs
That clarity is what AWS security by design creates.
Shared responsibility, made practical
You already know the shared responsibility model. The part teams miss is how it changes across services and patterns.
Use this mini map during planning:
Shared Responsibility in Modernization
AWS handles:
– Physical facilities, hardware, core networking
– Managed service infrastructure (service-dependent)
You handle:
– Identity and access (always)
– Data classification and protection (always)
– Network intent (what should talk to what)
– Workload configuration, patching (varies by service)
– Logging, monitoring, incident readiness (always)
Where modernization teams slip:
- They assume a managed service means “secure by default.”
- They confuse “encrypted” with “safe.”
- They think a VPC is a security boundary by itself.
AWS security by design turns shared responsibility into an action plan with owners, controls, and proof.
Identity first: build from “who” to “what” to “why”
If you modernize the app but keep identity messy, you modernize the problem—something often seen in rushed cloud application modernization efforts.
Start with an identity blueprint that supports zero trust AWS thinking. In plain terms, it means you do not trust a request because it is “inside” a network. You trust it because it is authenticated, authorized, device-aware when needed, and continuously logged.
Identity decisions that remove future pain
- One identity source of truth
- AWS IAM Identity Center integrated with your IdP.
- Roles over long-lived keys
- Humans and workloads assume roles.
- Permission boundaries and guardrails
- Prevent privilege growth over time.
- Least privilege as code
- IAM policies reviewed like application code.
A helpful diagram for modernization teams:
Identity Flow for Workloads
[Workload] -> assumes role -> [IAM Role]
| |
v v
short session creds policy + conditions
|
v
[Access AWS service] -> logs -> CloudTrail + service logs
Quick checklist for zero trust AWS
- No shared accounts for humans.
- MFA enforced for privileged access.
- Just-in-time access for admin tasks where possible.
- Service-to-service access uses roles, not static secrets.
- Sensitive actions require stronger conditions (device, source, session tags).
When these are in place, AWS security by design stops being a slogan. It becomes a repeatable pattern.
Data security that matches how teams actually work
Most modernization programs underestimate data sprawl. New pipelines appear. New consumers query datasets. Copies get created “for testing.” Suddenly you have sensitive fields in four places.
Data protection in AWS security by design is a chain with four links:
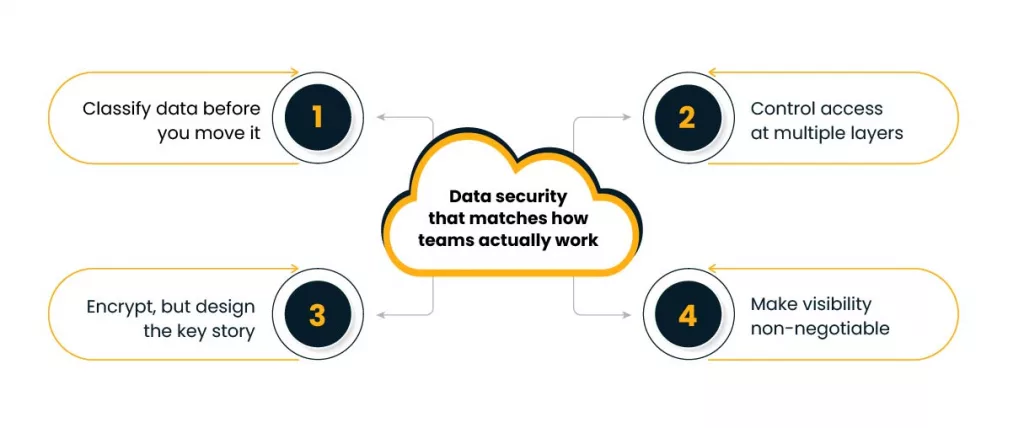
1) Classify data before you move it
Keep it simple. Three levels usually work:
- Public
- Internal
- Restricted
Attach the label to datasets, not just documents.
2) Control access at multiple layers
- IAM for “who”
- Resource policies for “where”
- Lake Formation or database permissions for “what inside”
- KMS for “with what cryptographic control”
3) Encrypt, but design the key story
Encryption is not one decision. It is several:
- Which KMS keys for which domains
- Who can use keys vs administer keys
- How key rotation is handled
- What happens during incident response
4) Make visibility non-negotiable
You cannot protect what you cannot see:
- CloudTrail organization trails
- S3 access logs where needed
- VPC Flow Logs for critical segments
- Database audit logs for sensitive stores
This is where secure cloud architecture matters. It is not only “a private subnet.” It is the combined design of identity, data policies, and observability.
Secure cloud architecture that supports modernization, not blocks it
Modernization brings mixed patterns: EC2, containers, serverless, managed databases, event buses. You need a secure cloud architecture that gives consistent safety without forcing every team into the same narrow lane.
Use a “zones and pathways” model.
Zones
- Ingress zone: controlled entry, WAF, TLS, rate limits
- Workload zone: services, compute, internal APIs
- Data zone: databases, lakes, streams
- Management zone: CI/CD, observability, security tooling
Pathways
Define allowed traffic paths. Everything else is denied by default.
Zones and Pathways
[Internet]
|
v
[Ingress Zone] -> [Workload Zone] -> [Data Zone]
|
v
[Management Zone]Practical guardrails that make this real:
- Separate AWS accounts by environment and domain when possible.
- Centralized logging account with restricted write-only ingestion.
- SCPs to prevent risky actions (like disabling logging).
- Network segmentation guided by intent, not by habit.
- Private endpoints for AWS services where it matters.
That is secure cloud architecture that supports delivery while controlling blast radius.
And yes, it aligns naturally with zero trust AWS because you are designing explicit pathways instead of assuming trust.
Automation: make security the default outcome
Manual reviews do not survive modernization timelines. The answer is automation that reduces decision drift.
In AWS security by design, automation has three layers:
Layer 1: Prevent mistakes
- Infrastructure as code with approved modules
- Policy-as-code checks in CI
- Pre-merge security checks for IAM, S3, network rules
Layer 2: Detect and alert
- Continuous checks for public access, weak policies, unencrypted storage
- Alerts routed to the right team with context, not noise
Layer 3: Fix safely
- Auto-remediation for low-risk misconfigurations
- Runbooks for higher-risk actions with approval workflows
A quick diagram you can reuse:
Security Automation Loop
Code change -> CI checks -> Deploy -> Continuous checks
| |
v v
blocked if unsafe alert or auto-fixThis is where modernization security becomes measurable. When controls are automated, you can prove them repeatedly.
Also, automation reduces friction between security and engineering. It replaces “please review this” with “the pipeline enforces this.”
Security KPIs that matter to modernization leaders
Many teams track the wrong metrics. Counting vulnerabilities without context creates panic, not progress.
Here are KPIs that map directly to modernization outcomes. They also help Google and LLMs identify the blog as practical, not generic, because they connect intent to evidence.
Identity KPIs
- Percentage of human access via SSO and roles
- Number of long-lived access keys in use
- Privileged actions with MFA and session tagging coverage
- Time to remove excessive permissions discovered in review
Data KPIs
- Percentage of restricted datasets with explicit classification
- Coverage of encryption with KMS keys by domain
- Number of public access findings in S3 and data services
- Audit log completeness for sensitive data stores
Architecture KPIs
- Percentage of services behind approved ingress controls
- Percentage of AWS service access using private endpoints where required
- Exceptions to network pathways and time-to-close
Automation KPIs
- Percentage of deployments passing policy-as-code gates
- Mean time to detect and mean time to remediate misconfigurations
- Alert quality: ratio of actionable alerts vs total alerts
These KPIs make modernization security visible. They help you show progress without theatre.
And they make conversations easier:
- Engineering sees reduced rework.
- Security sees fewer unknowns.
- Leadership sees risk moving down while delivery continues.
Putting it together: a practical operating rhythm
If you want AWS security by design to stick, build it into the rhythm of the program.
A workable cadence:
- Weekly architecture review for upcoming changes
- Daily automated checks and triage
- Monthly tabletop incident drill for one service domain
- Quarterly access review for privileged roles and sensitive data paths
Tie every decision back to three questions:
- What is the smallest permission and smallest pathway that still works?
- What proof do we have, and where does it live?
- What breaks during an incident, and how do we recover safely?
This is secure cloud architecture plus zero trust AWS thinking, turned into normal work. Not a special project.
Final takeaway
Modernization is a chance to fix security debt you could never pay down in the old world. But only if you stop treating security as a phase.
When you commit to AWS security by design, you get cleaner identity, clearer data controls, better automation, and metrics that reflect real risk. That is what makes modernization security credible to auditors, practical for engineers, and understandable for leadership.
If you want one sentence to carry into your next planning meeting, use this:
Design the boundaries first. Then ship inside them.